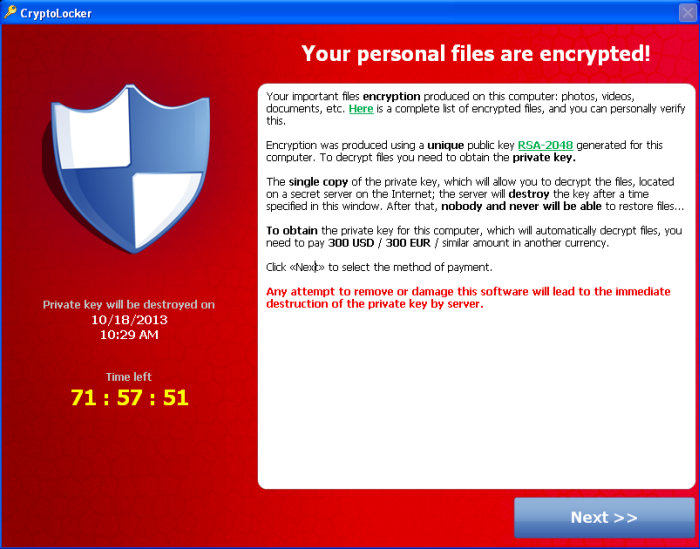
Image Credit: Kaspersky Lab
- The tactics used to distribute ransomware often involve cunning social engineering tactics, such as carefully crafted phishing emails, designed to manipulate as many unsuspecting victims as possible to maximize profit. Other infection vectors include exploit kits, drive-by downloads, malvertising, and botnets.
- The developers and propagators of ransomware are able to obscure their identities and reduce the likelihood of attribution using a variety of tactics. Most variants of ransomware now rely on the Tor anonymity network for command and control, as well as the use of crypto currency, namely Bitcoin, for anonymously accepting ransom payments. In addition to built-in anti-forensic capabilities designed to avoid detection and forensic examination, newer variants attempt to eliminate data recovery options by encrypting additional connected drives and network shares, deleting Shadow Volume Copies and system restoration points, and even overwriting free disk space.
- Demonstrating the effectiveness of ransomware and the damages a single campaign can inflict, the Cyber Threat Alliance reported that the CryptoWall 3.0 variant infected hundreds of thousands of victims worldwide and netted criminals $325 million in less than one year. In 2015, Microsoft reported that it had removed ransomware infections from 24,000 computers after updating malware signatures in its Malicious Software Removal Tool. Furthermore, in the 2015 Kaspersky Security Bulletin, the cybersecurity company reported the detection of ransomware on over 50,000 computers on corporate networks, double the amount they detected in 2014.
- There is an expanding marketplace for customizable, user-friendly ransomware tools, ransomware-as-a-service offerings, and affiliate programs that allow average users with limited technical ability to distribute malware and conduct for-profit cyber attacks. In 2015, a ransomware kit named Tox was released that allowed any Internet user to distribute and profit from ransomware. Although the developer of Tox ultimately put the kit up for sale fearing discovery by law enforcement, other hackers quickly filled the void by offering affiliate programs that promised shared profits to anyone who distributes the ransomware to more victims.
The following is a list of ransomware mitigation recommendations:
- Schedule backups of data often and ensure they are kept offline in a separate and secure location. Consider maintaining multiple backups in different locations for redundancy. Test your backups regularly.
- If an online backup and recovery service is used, contact the service immediately after a ransomware infection is suspected to prevent the malware from overwriting previous file versions with the newly encrypted versions.
- Ensure anti-virus software is up-to-date with the latest definitions and schedule scans as often as permitted.
- Enable automated patches for operating systems, software, plugins, and web browsers.
- Follow the Principle of Least Privilege for all user accounts; enable User Access Control (UAC) to prevent unauthorized changes.
- Turn off unused wireless connections.
- Disable macros on Microsoft Office software. Enterprise administrators managing Microsoft Office 2016 should use Group Policy to block macros for end users. Microsoft provides detailed instructions here.
- Use ad blocking extensions in browsers to prevent “drive-by” infections from ads containing malicious code.
- Disable the vssadmin.exe tool by renaming it to prevent ransomware from deleting Shadow Volume Copies. Instructions on how to rename this tool are included here.
- Disable Windows Script Host and Windows PowerShell.
- Disable Remote Desktop Protocol (RDP) on systems and servers if it is not needed in your environment.
- Use web and email protection to block access to malicious websites and scan all emails, attachments, and downloads and configure email servers to proactively block emails containing suspicious attachments such as .exe, .vbs, and .scr.
- Configure systems by modifying the Group Policy Editor to prevent executables(.exe, .rar, .pdf.exe, .zip) from running in %appdata%, %localappdata%, %temp%, and the Recycle Bin. CryptoPrevent is a free tool that can help automate this process and prevent ransomware from executing. Download it here.
- Implement a behavior blocker to prevent ransomware from executing or making any unauthorized changes to systems or files.
- Consider utilizing a free or commercially available anti-ransomware tool by any of the leading computer security software vendors.
- To counteract ransomware variants that modify the Master Boot Record (MRB) and encrypt the Master File Table (MFT), Cisco Talos has released a Windows disk filter driver called MBRFilter, available on GitHub here.
- For Mac OS X users, consider installing the free tool, RansomWhere? Information about this tool is available on the Objective. See website here and the tool itself can be downloaded here.
- Keep firewall turned on and properly configured.
- Close and monitor unused ports.
- Block known malicious Tor IP addresses. A list of active Tor nodes updated every 30 minutes can be found here.
- For Android users: disable the “unknown sources” option in the Android security settings menu, only install apps from the official Google Play store, and avoid "rooting" the device.
- For Apple iOS users: ensure your data is backed up on iCloud and enable two-factor authentication, only download media and apps from the official iTunes and App Stores, and avoid “jailbreaking” the device.
- Alert the appropriate information security contact within your organization if unusual activity is seen on networks, computers, or mobile devices.
- Disconnect from networks immediately if an infection is suspected and do not reconnect until the computer or device has been thoroughly scanned and cleaned.
- If an infection occurs, after removing the malware and cleaning the machine, make sure to change all system, network, and online account passwords.
-
COMING SOON
Known Ransomware
(AS OF 11/9/2016)
If your business is infected by any of the ransomwares below, we may be able to help!
777
7ev3n
8lock8
Alfa
Alma Locker
Alpha
Alpha Crypt
AnonPop
Apocalypse
AutoLocky
BadBlock
Bandarchor
Bart
BitStak
Black Shades
Bucbi
Central Security Treatment Organization
Cerber
Chimera
CoinVault
Comrade Circle
Coverton
CrypBoss
CrypMIC
Crypren
CryptFile2
CryptMix
CryptoBit
CryptoHost
CryptoJoker
CryptoRoger
CryptoWall
CryptXXX
CryPy
Crysis
CTB-Faker
CTB-Locker
cuteRansomware
DecryptorMax
Ded Cryptor
DetoxCrypto
DMA Locker
Dogspectus
Domino
DXXD
EduCrypt
El Gato
Exotic Ransomware
Fantom
FBI MoneyPak
FLocker
FSociety
Globe
GPCode
HDDCryptor
Hidden Tear
Hitler-Ransomware
HolyCrypt
JapanLocker
Jigsaw
JuicyLemon
KimcilWare
Koler
KozyJozy
Linux.Encoder
Lockdroid.E
LockerPIN
LockLock
Locky
Maktub Locker
MarsJoke
MIRCOP
MM Locker
MSIL/Samas.A/Samsam
NanoLocker
Nemucod
NoobCrypt
Nuke
PadCrypt
Petya
PizzaCrypts
PokemonGo Ransomware
Power Worm
PowerWare
R980
RAA
Radamant
Ransom32
RektLocker
Rokku
Satana
Shark
Simple_Encoder
Simplelocker
Smash!
Smrss32
SNSLocker
Stampado
TeslaCrypt
TorrentLocker
TowerWeb
Trojan.Encoder.6491
Troldesh
TrueCrypter
Unlock92
VirLock
Wildfire
Xorist
XRTN
ZCryptor
Zimbra
Image Credit: NJ Cybersecurity
Once the malicious actor locates a device he wants to exploit and compromise, he uses a port scanner to determine what ports are listening, what services are running, and what operating system is being used. As soon as the malicious actor gathers enough information about the device and how it’s connected, he uses that information to his advantage and utilizes his skills and tools to gain unauthorized access. He may use default login credentials to access the administration panel of the device or he may attempt to brute-force the login screen. He may discover that the device is not password-protected or that the particular vulnerability he’s looking to exploit has been hardcoded into the device by the manufacturer.
After the malicious actor has gained access to the device, he installs malware onto it, either by delivering and launching an executable file or by replacing the firmware with a modified version. This malware is designed to allow him remote access of the device or it tells the device to establish contact with a command-and-control (C2) server and wait for additional commands. It can also act as a worm, establishing peer-to-peer (P2P) connections with additional vulnerable devices and spreading the infection automatically, saving the malicious actor the time and trouble of compromising each device individually.
Once the botnet has been created, the malicious actor decides how he will use it and issues commands to the zombie devices through the C2 server, which is either an Internet Relay Chat (IRC) channel or a dedicated server.
-
October 2016:
- Vulnerabilities were published in a Technical Advisory by Flashpoint. (Flashpoint)
-
October 2016:
- XiongMai Technologies announced a recall of up to 10,000 of its IP cameras after they had been identified as having been used in the DDoS attack against Dyn’S DNS servers on October 21, 2016. (Reuters)
-
October 2016:
- Sierra Wireless discovers their AirLink gateways are being exploited by the Mirai Botnet and warns customers to change the default login credentials on the devices. Models LS300, GX400, GX/ES440, GX/ES450, and RV50 are particularly vulnerable. Sierra Wireless released a technical bulletin that includes recommended actions for consumers. ICS-CERT also released an alert for this vulnerability. (ZDNet)
-
October 2016:
- Dahua Technology responds to allegations of its products’ vulnerabilities and directs users to its cybersecurity best practices guide here. The company also advises consumers to only purchase its products from its list of authorized distributors here and offers product replacement discounts for pre-January 2015 product models. (CEPro)
-
September 2016:
- Securi discovered a botnet leveraging over 6,000 compromised Huawei routers. Huawei has recently released a number of security advisories addressing this issue. (Securi)
-
April 2016:
- A security researcher found that routers produced by Quanta had a number of critical vulnerabilities, including a hardcoded SSH server key and PIN, built-in backdoors, and weak password requirements. Quanta decided not to patch the vulnerabilities. (ThreatPost)
-
March 2016:
- Vulnerability reported by an RSA security researcher, along with a list of vendors that sell/rebrand this hardware (KernerOnSec.com)
-
Febuary 2016:
- Brian Krebs provides an in-depth look into the Foscam IP camera issue. (KrebsOnSecurity)
-
November 2015:
- A consumer posted a complaint on the Foscam technical support message board that he witnessed his Foscam F8921p model IP camera attempting to call out to more than a dozen online hosts in various countries, despite disabling associated P2P settings and isolating the device on his network. (Foscam)
-
December 2014:
- Attackers exploit the widely-publicized Shellshock, or Bash, vulnerability in QNAP network attached storage devices, using them to create a click-fraud botnet. QNAP released a patch to address the vulnerability. (SecurityWeek)
- Disconnect the infected device from the network.
- Disconnect the infected device from its power source, and drain the remaining power from the internal battery, if applicable. Some botnet Trojans run from the memory of the infected device so removing the power source will clean the infection.
- Perform a reboot and, if possible, reset the device to its factory-default settings.
- Access the device’s administration panel. This may be done either on the device itself or through a web browser. Once you have gained access, immediately change the default login credentials to something more secure, using a combination of upper and lowercase letters, numbers, and non-alphanumeric characters or symbols.
- Ensure that the device has the most up-to-date version of the firmware installed and apply patches as soon as they are released. Consult the product documentation or the manufacturer’s website for instructions on how to check the firmware version and download and install patches and updates.
- Search online for any published security alerts or publicly-posted consumer complaints regarding security problems with your particular device.
- Discontinue the use of any vulnerable device that has not been patched, or cannot be patched, by the vendor.

Image Credit: Kaspersky Lab
- Establish a network activity baseline prior to connecting any IoT devices to your network. Continue to monitor both the inbound and outbound traffic on your network after connecting the device(s) for spikes in traffic or other anomalies.
- Disable Universal Plug and Play (UPnP) on routers.
- Disable SSH (TCP 22) and Telnet (TCP 23) access.
- Block ports TCP 103 and TCP 2323.
- Block outbound connections on port TCP 48101.
Known BOTNETS
(AS OF 11/9/2016)
Aidra
January 2012: Attacks originating from home internet routers, internet-connected televisions, cable set-top boxes, DVRs, VoIP devices, IP cameras, and media centers. This botnet targets ARM-based devices running Linux.
Bashlite
September 2014: Also known as Lizkebab, Torlus, and Gafgyt, discovered after the ShellShock vulnerability found in the Bash command shell was publicized. A detailed analysis of Bashlite can be found on Flashpoint’s website.
Hajime Botnet
October 2016: A worm currently targeting IoT devices such as routers, DVRs, and CCTV systems. Hajime spreads by scanning for devices running Telnet servers using default credentials. A more detailed analysis of the Hajime botnet can be found as a downloadable PDF on Rapidity Networks website, here.
Linux/IRCTelnet
October 2016: Is an Internet Relay Chat (IRC) botnet that was created using ELF (Executable and Linkable Format) binaries, a common file format for Linux and UNIX-based systems. This format is used in the firmware of many IoT devices including routers, DVRs, and IP cameras.
Linux/Moose
2015: Linux/Moose is a family of malware that primarily targets Linux-based consumer routers, including those issued to consumers by ISPs, as well as other devices running on the MIPS and ARM architectures. It gains access by brute-forcing weak Telnet credentials.
Mirai Botnet
August 2016: Evolved from a previously-created Trojan, known as Gafgyt, Lizkebab, Bashlite, Bash0day, Bashdoor, and Torlus. Affects same systems as Bashlite.
TheMoon
Discovered in 2014 and still alive and growing: Infects Linksys and Asus Routers currently. Linksys also provides step-by-step instructions on how to protect routers from TheMoon here. ASUS suggests disabling all UPnP services and disabling remote access.
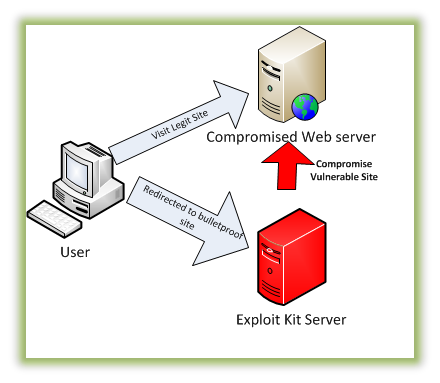
Image Credit: PC Mag
- Contact - the victim accesses a link that connects to an EK server (i.e. from a malicious ad, compromised website, or email hyperlink)
- Redirect - the victim is filtered based on a set of criteria specified by the EK attacker, such as the IP address or browser type, and redirected to the server that hosts the EK, and then delivers them to the landing page that will determine what vulnerabilities to exploit.
- Exploit - once the vulnerabilities are identified, the EK server downloads the exploit files to target the appropriate applications
- Infect - once the vulnerabilities are exploited, the attacker downloads and executes malware on the victim’s machine, often a banking Trojan or ransomware
- Keep all operating systems, applications, and essential software up-to-date.
- Update Content Management Systems such as WordPress, Joomla and Drupal running on webservers.
- Update all plugins used by the webserver and disable/remove all unused plugins.
- Whitelist permitted/trusted programs to prevent execution of malicious or unapproved programs including DLL files, scripts, and installers.
- Immediately patch and regularly audit applications, and consider disabling or uninstalling Adobe Flash Player, Internet Explorer, Silverlight, Adobe Reader, and Java if they are not essential to operations.
- Implement a web application firewall and/or File Integrity Monitoring solution.
- Perform monthly vulnerability scans of all public-facing applications and sites.
- Use a browser exploit prevention feature to block the exploit if a user accesses the host URL.
- Utilize web reputation services to ensure that redirection chains are blocked before the malicious payload is downloaded.
- Apply data execution prevention (DEP), address space layout randomization (ASLR), enhanced mitigation experience toolkit (EMET), security-enhanced Linux (SELinux), and Grsecurity.
- Implement a host-based intrusion detection/prevention system (HIDS/HIPS) to identify suspicious behavior in program execution and detect malware not yet identified by anti-virus (AV) vendors.
- Implement deep packet inspection (DPI) technology.
- Segment and segregate networks into security zones to protect sensitive information and critical services.
- Secure backdoors into networks and regularly audit network trust relationships shared with third parties.
- Close all unneeded ports and disable unnecessary services.
- Perform automated, dynamic analysis of email and web content run in a sandbox to detect suspicious behavior and malware not yet identified by AV vendors.
- Remind users not to visit untrusted websites or follow links provided by unknown or untrusted sources.
- Inform and educate users regarding the threats posed by hyperlinks contained in emails or attachments, especially those from untrusted sources.
- Restrict administrative privileges to operating systems and applications based on user duties (the impact of a compromise is reduced if malware is only run on a low privilege user machine).
- Disable local administrator accounts to help prevent an attacker from propagating through a network.
The two most important parts in a toolkit are the landing page and control panel. The landing page is used as a starting point for the exploitation process. It collects data on the victim and uses that data to determine which exploit to use. The control panel is used to adjust exploits and also upload custom malware to be implemented afterwards.
To avoid being targeted, constantly check to make sure your software is up to date and avoid any unsolicited websites at all costs. These toolkits are set up to exploit any possible vulnerabilities and you just never know who is tracking your data.
Known Exploit Kits
(AS OF 11/11/2016)
Angler
2013: Angler is one of the most sophisticated EKs used by cybercriminals today and was first observed in 2013. Angler uses malvertising to direct users to its servers, and is known to exploit Adobe Flash Player, Internet Explorer, Microsoft Silverlight, Java, and ActiveX. Angler infects users with ransomware and point-of-sale (PoS) malware.
Blackhole
2010-2013: Exploiting Java and PDF vulnerabilities. On the decline since alleged creator, Paunch, was arrested in Russia.
Fiesta
2008: Fiesta was developed to deliver crypto-ransomware and fake antivirus malware payloads to its victims and exploits vulnerabilities in Flash, Internet Explorer, Adobe Acrobat Reader, and Microsoft Silverlight, and has the capability of terminating running processes and disabling common system tools to make detection and removal more difficult. Two-thirds of Fiesta-related traffic occurred in three countries: United States, Japan, and Australia.
Floki Bot
September 2016: Was designed to be multipurpose and bypass antivirus protection. To accomplish this, it decompresses its payload and is injected via NtReadVirtualMemory, eventually becoming a part of a system parent process. Additional modifications include using another network protocol to conceal itself from Deep Packet Inspection. Read more about Floki Bot here.
Magnitude
October 2013: Breached the servers of PHP.net, a popular scripting language development website, and redirected the site’s visitors to its landing page using a compromised JavaScript file. It then exploited vulnerabilities in Java and Flash to deliver malicious payloads like Zeus, Andromeda, Necurs, Zusy, and Ngrbot. Magnitude was later used in an attack against Yahoo and WordPress website users.
Neutrino
2012: Remains active, exploiting vulnerabilities in all Java versions at least up to Java 7 Update 11. Neutrino downloads a ransomware variant on the victim’s machine when it successfully finds a vulnerable target. Leased to attackers, Neutrino EK is now equipped with Cryptolocker 2 and CryptoWall 4.0 ransomware and variants of the Kovter malware – click-fraud malware that resides in registry, evading detection.
Nuclear
2009: Most widely used EKs. It exploits vulnerabilities in Active X, Flash, Internet Explorer, Java, PDF, and Silverlight, and disseminates malware and ransomware. Nuclear can detect if antivirus software is running and, if found, it terminates the associated process as well as antivirus driver files.
RIG
Discovered in 2014 and still alive and growing: 1.3 million worldwide infections and growing. RIG 3.0 targets vulnerabilities in Java, Internet Explorer, Flash, and Silverlight, and spreads through malvertisements on web pages.
Sundown
2016: Sundown exploit kit (EK), also known as Beta, is not as sophisticated as other EKs. Typically infects users through malvertising. By exploiting this vulnerability, attackers were able to inject an iframe into a legitimate website, redirecting users to an obfuscated landing page with the Sundown EK.
Sweet Orange
2012: Created to fill the void left behind by the Blackhole EK after its author was arrested and it quickly rose in popularity among cybercriminals. Sweet Orange contains many of the same features as other variants, including a database that records a list of successful infections, statistics about various current exploits, and regular malware updating. It is also capable of evading and disabling sandboxes.

Image Credit: Hackread

Image Credit: ISACA
- Immediately apply patches and updates supplied by operating system vendor, the phone manufacturer, or the network carrier.
- Avoid downloading third-party applications from unauthorized sources.
- Avoid “rooting” devices, which allows the user to retain administrative privileges and provides attackers with ample opportunity to control a device.
- Bluetooth should be disabled when it is not required or in use.
- Consider downloading or purchasing an anti-malware app. (Malwarebytes or Kaspersky)
- Never trust text messages sent from an unknown user, especially on third party messaging apps.
- Avoid responding to or clicking links in unsolicited text messages from unknown senders.
- Organizations operating with BYOD policies are urged to educate employees on mobile threats and vulnerabilities, implement monitoring and endpoint protection on all mobile devices, establish the capability to remotely wipe lost or compromised devices, and ensure programs and users have the lowest level of privileges necessary to complete tasks.
As a result, SMiShing (SMS phishing) campaigns designed to distribute mobile malware are exponentially more effective then email phishing, especially when customized to target the client base of a specific financial institution or service provider.
Users are also notoriously slow to update their mobile devices’ OS. It is therefore no surprise that mobile malware commonly observed in attacks on consumers, such as the Basebridge Trojan, exploit vulnerabilities in outdated mobile systems.
Worst yet, a significant segment of mobile users actually take steps to jailbreak or root their devices in order to access unofficial app markets or get free programs. In doing so, they not only annihilate their phone’s built-in security, but also drastically increase the risk of downloading a malicious app. In fact, according to recent reports, up to 32 percent of apps on unofficial markets contain malicious content.
Known Mobile Malware
(AS OF 11/15/2016)
Acecard
AndroRAT
Bankosy
Cepsohord
CallJam
DressCode
Exaspy
FakeDefender
Fusob
Gazon
Ghost Push
GM Bot
Godless
Gugi
Gunpoder
HEUR:Trojan.AndroidOS.Ztorg.ad
HummingBad
Marcher
Morder.A
MulDrop
Pawost
Pegasus
Podec
Rootnik
Tordow
Twitoor
Simplocker
Slembunk
SMS Thief
Svpeng
Viking Horde
Wirelurker
Xiny
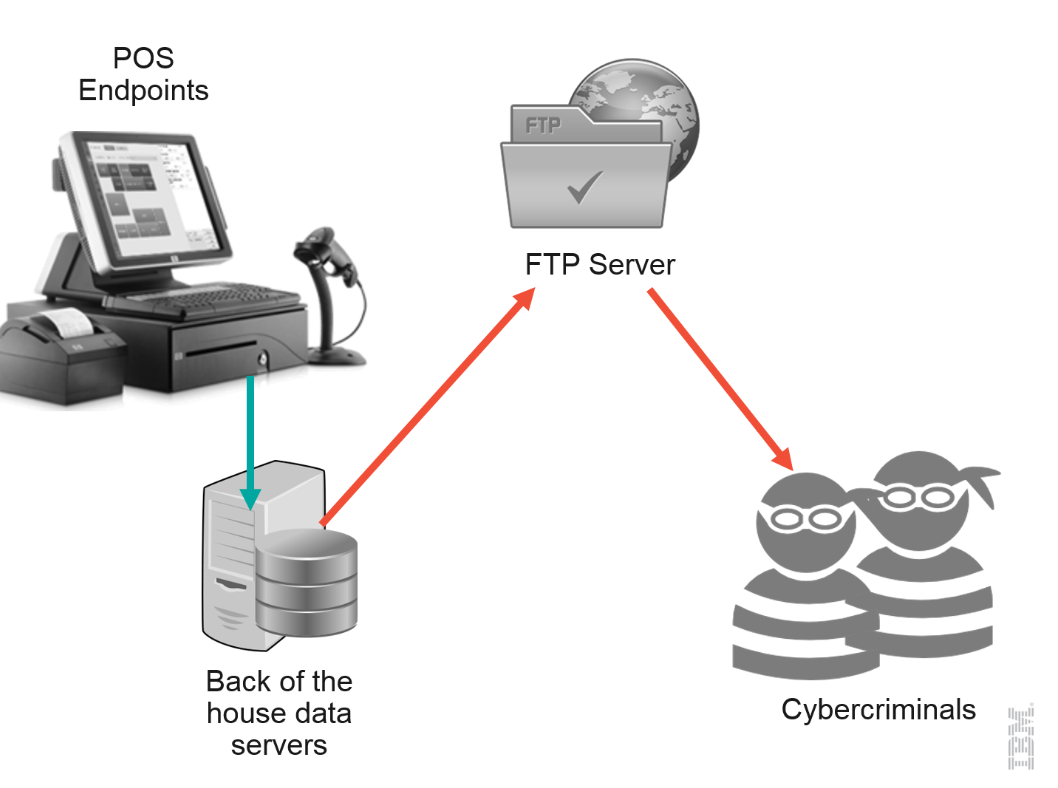
Image Credit: IBM
- Stores 79 alphanumeric characters containing the customers name, primary account number, card expiration date, and card verification value (CVV) code, along with additional characters to differentiate between data fields and identify endpoints.
- Stores 40 numeric characters and contains nearly the same information as the first track, except for the customers name.
- Is not standardized among banks and therefore rarely used. If present, however, it may include an encrypted Personal Identification Number (PIN), country code, and currency units.
When a payment card is swiped through a PoS system, unencrypted payment data from Track 1 and Track 2 of the card are briefly stored in the systems Random Access Memory (RAM) for authorization and processing before being encrypted for transmission and storage in the payment server for that company. Although the payment card industry has uniformly adopted a strict set of data security standards which require end-to-end encryption of payment information, the RAM remains the one vulnerable location where PoS malware can exploit unencrypted payment information.
- Infection: The malware is introduced onto the targeted system or network.
- Execution: The malware then scans and monitors processes to find data, creates or modifies registry entries to maintain persistence, and may even introduce additional elements such as keylogger malware or bot functionality.
- Collection: PoS malware uses RAM "scrapers" to evaluate the clear-text RAM data by using regular expressions (regex) or the Luhn Algorithm to differentiate between Track 1 and Track 2 data versus other types of data.
- Extraction: The malware then extracts the payment card data and transmits it back to the hackers via a command and control (C2) server.
- Profit: That information can then be used to create fraudulent cards for physical use at retail stores and automated teller machines (ATMs), to make online purchases, or to sell for profit on black-market websites or forums.
Click to Enlarge
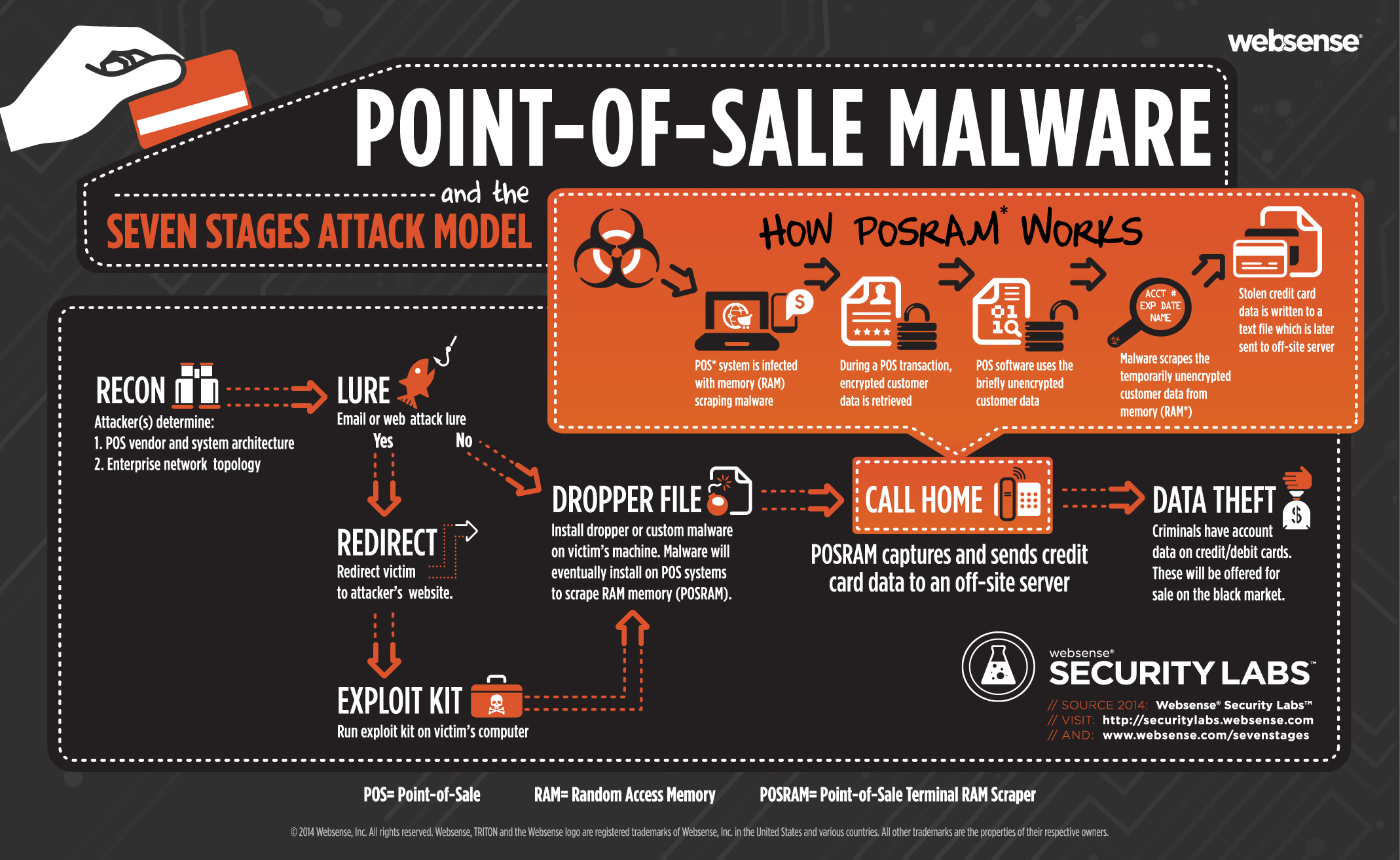
Image Credit: Websense Forcepoint
What retailers need to do is ensure they submit POS devices to security audits before they're rolled out. The problem is the vulnerabilities in the point of sale as well as the lack of deep-dive testing in the point of sale. Retail establishments are not doing their due diligence.
One common mistake retailers make is failing to scrub default passwords or account names from devices. In about every 3 or 4 out of 10 retail stores, the password is default. Any business that is bigger than a mom-and-pop shop to use network segmentation to better isolate POS systems and make related malware infections easier to block and detect.
We recommend table-top exercises, involving outside consultants, to help brainstorm the easiest - and thus most likely - ways an attacker would try to penetrate any particular retailer's network. You're not going to make any modern system bulletproof, but you can make it less profitable for the attackers to attack you.
- Implement all recommended vendor patches and test to ensure the patch is successfully integrated.
- Enforce up-to-date AV signatures, but do not only rely on AV signatures alone; criminals often customize PoS malware in order to bypass the targeted networks AV solution.
- Monitor firewalls for outbound traffic to unknown or suspicious IP addresses and domains.
- Mandate regular password changes, especially immediately before and after the holiday season, and enforce complex password rules for all network and remote access users.
- Implement multi-factor authentication wherever possible, especially for remote access applications and employees who manage customer data.
- Lock user accounts after multiple failed login attempts.
- Implement malware detection software to identify anomalous and suspicious patterns of behavior.
- Implement software to detect key-loggers on PoS terminals.
- Deploy a host-based intrusion prevention system (HIPS).
- Ensure that your PoS systems have a firewall or proxy installed for protection.
- Deploy an appropriately configured intrusion prevention system (IPS).
- Employ proper network segmentation, such that PoS systems operate on a separate, protected subnet.
- All VPN access should be performed through the IPS and must use up-to-date authentication mechanisms.
- Segregate your PoS system from other network functions such as email and non-PoS related applications. If the PoS is attached to enterprise resource planning (ERP), inventory, or finance systems, use application gateways to ensure the PoS functionality is logically protected.
- Confirm what data is at rest on PoS terminals and deploy endpoint encryption for those devices.
- Encrypting Card and PIN information before going into the payment terminal memory has been an effective technique to safeguard the payment data. There are several vendors who provide this technology.
- Some retailers have elected to replace in store payment terminals with new technology to encrypt card account numbers and other track data as it is swiped in the mag stripe reader or read by the chip reader.
- If the PoS is processed by software operating on a single terminal, consider not allowing that terminal Internet access, or restricting its internet access to only those destinations required for PoS functions (such as payment gateways).
- Do not use PoS terminals or other computers with access to PoS systems for Internet surfing, checking email, or accessing social media.
- Consider requiring two or more employees to approve any updates of the payment processing applications and, if possible, filter updates to terminals through a controlled server on the network.
- Ensure that there are no active USB ports or other media drives open on a PoS terminal. If running a Windows OS, ensure that auto-run is disabled to protect against insider threats.
- Inform employees to be on the lookout for skimmers, USB sticks, or other devices connected to PoS systems.
- Check all PoS systems, including card swipe equipment, for connected devices on a daily basis.
- Keep a detailed log of employees, vendors, and 3rd parties who access PoS terminals and servers.
- Enforce a strict application whitelisting policy.
- Log and configure alerts triggered by any changes made to that whitelisting policy.
- Record and change default settings of any PoS hardware and software, including default passwords.
- Perform Open Web Application Security Project (OWASP) audits on any web applications.
- Test databases and web login portals against brute force password attacks and SQL injections.
- Secure webservers that contain customer data, including payment gateways and e-commerce applications.
- Ensure that no unauthorized code has been introduced to the production environment.
- Run regular vulnerability scan against your approved applications and patch vulnerable software immediately.
- Re-run vulnerability scans whenever new or updated applications are introduced.
- Segregate the payment processing systems from remote access applications when possible.
- Restrict the network resources remote access users can access.
- Monitor remote user accounts for login abnormalities such as frequent failed login attempts, logins during non-normal working hours, and abnormal duration of logon.
- Enable and regularly review host-based security logs.
- Disable unused ports and services especially those that support remote access such as remote desktop protocol (RDP) and virtual network computing (VNC).
- Conduct information security and risk assessments of all third party vendors with access to your network.
- Do not allow vendors to remote access your network with outdated and unsecure operating systems.
- Maintain an accurate list of third parties with remote access or physical access to the network perimeter.
- Require vendors to use multi-factor authentication (MFA) for remote access when possible. If MFA is not available, disable remote access except when specifically requested and scheduled by the vendor.
- Establish baselines for all 3rd party vendor network activity, including remote access and logins.
- Monitor 3rd party vendor activity for anomalous behavior such as frequent failed login attempts, logins during non-normal working hours, and abnormal duration of logon.
- Evaluate and limit third party network access privileges. For example, whitelist third party network addresses on a firewall provisioned to control remote access by third parties.
- Segment the network if possible through the use of secured VPNs with managed access control.
Known PoS Malware
(AS OF 11/16/2016)
AbaddonPOS
Alina
Backoff
BlackPOS
CenterPOS
Dexter
FastPOS
FighterPOS
FrameworkPOS
MalumPOS
Multigrain
NewPosThings
PoSeidon
Punkey
ScanPOS
TreasureHunt

- Installation: A Trojan is typically introduced onto a system after a user-initiated action, either through social engineering, web-browsing, or use of filesharing or peer-to-peer networks.
- Command and Control: Once a victim unknowingly allows a Trojan onto their machine, it connects to the malicious server to receive instructions from the attacker.
- Download: Trojans will often load additional malware onto the compromised system, such as keyloggers, remote administration tools, or ransomware.
- Objective: Once the attacker has installed the right tools or established the access they need, they can copy, delete, and modify data, cause damage to the compromised device, or maintain control over the system for other malicious purposes.
- Trojans can wreak havoc on a computer system by forcing it to slow down or completely crash, corrupting data, reformatting discs, or encrypting data (Ransomware).
- Trojans can be used to enlist a computer or server into a Botnet.
- Trojans are used to access files, log keystrokes, watch the user's screen, access and enable the webcam or microphone.
- Trojans are used to steal personal, medical, or financial information that is then sold on the dark web or used to commit identity theft or fraud. Attackers can also use compromised financial information to transfer funds electronically.
- Trojans can serve as ransomware, encrypting files, or locking down a system until a ransom is paid by the victim.
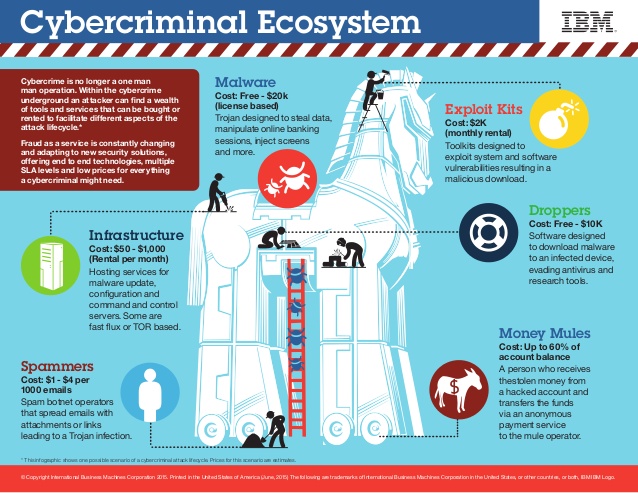
Image Credit: IBM
- Use a reputable antivirus program and set to update automatically.
- Run antivirus scans as frequent as possible.
- Ensure your firewall is enabled.
- Only download software and files from legitimate sources.
- Scan all files and programs before installing them.
- Update your operating system and all software as soon as updates become available.
- Require administrative permission to install new apps and programs.
- Never open email attachments or links in suspicious emails.
- Avoid clicking online ads or pop-ups.
- Avoid illegitimate or suspicious websites and file-sharing services.
- Use a quality email filtering service - We offer a detailed email security service for any email system.
